ini ada beberapa saran yg bisa dicoba untuk mempercepat Squid. Silahkan komentar-komentar saya dicermati dan bereksperimen sedikit. Saya jamin Squid anda akan bekerja lebih cepat dg hit ratio bisa lebih dari 50%. Mohon teman-teman yg lain dibantu juga. Terima kasih dan jangan kaget kalau kinerja Squid anda naik drastis, he he he ….. Semoga bermanfaat ….
## Jika ada beberapa situs terdekat yg mungkin hanya 1 hop, di-by pass saja supaya kerja Squid benar-benar utk yg jaraknya jauh
hierarchy_stoplist cgi-bin ? localhost domain-anda.com isp-anda.com domainku.web.id
acl QUERY urlpath_regex cgi-bin \? localhost domain-anda.com isp-anda.com domainku.web.id
no_cache deny QUERY
## Dari pengalaman 6 MB akan lebih cepat dan biarkan Squid bekerja lebih keras lagi
cache_mem 6 MB
cache_swap_low 98
cache_swap_high 99
## Maksimum obyek di hardisk dan di memori diupayakan lebih besar shg byte hit lebih tinggi (bisa dinaikkan lagi jika hardisk berkecepatan tinggi dan jumlahnya banyak dg memori yg lebih besar pula)
maximum_object_size 128 MB
maximum_object_size_in_memory 32 KB
## Jika memori 512 MB atau lebih besar silahkan cache diperbesar
ipcache_size 2048
ipcache_low 98
ipcache_high 99
## Utk heap replacement saya memakai LFUDA utk cache hardisk dan GDSF utk cache memori dg alasan di hardisk diprioritaskan obyek yg ukuran besar-besar dan di memori obyek yg ukurannya kecil-kecil utk disimpan
cache_replacement_policy heap LFUDA
memory_replacement_policy heap GDSF
## Idealnya ruang di hardisk yg anda pakai hanya sekitar 70% dari total krn semakin penuh Squid akan semakin pelan mencari tempat kosong, mis. utk cache 1 GB maka yg dipakai hanya 700MB (jangan 1GB dipakai semuanya). Jangan lupa hanya 1 direktori per drive krn faktor penghambat adalah kecepatan spindle hardisk lho, bukan terus dg memperbanyak direktori pada 1 hd akan mempercepat (hd orde milidetik, memori orde nanodetik). Jadi mending hardisknya banyak tapi ukurannya kecil-kecil daripada hanya 1 berukuran besar. Terus jika OS-nya Linux pakailah FS-nya Reiser (versi 4 tercepat) dg metode akses aufs. Diskd optimal di FreeBSD tetapi tidak di Linux lho. Jangan lupa di partisi tsb noatime dan notail diaktifkan spy tidak menambah ekstra write saat menulis atau membaca. Intinya hardisk adalah faktor penghambat terbesar di Squid.
## saran kira2 70% dari 16GB
cache_dir aufs /cachez 12000 28 256
atau (utk ruang 4GB-an per hardisk)
cache_dir aufs /cachehardisk1 3000 8 256
cache_dir aufs /cachehardisk2 3000 8 256
cache_dir aufs /cachehardisk3 3000 8 256
cache_dir aufs /cachehardisk4 3000 8 256
atau minimal di bawah ini supaya modifikasi tidak terlalu jauh
cache_dir diskd /cachez 12000 28 256 Q1=72 Q2=88
## Log utk info yg vital saja dan diusahakan file-file log ada di hardisk tersendiri spy tidak mempengaruhi kecepatan direktori cache utamanya
log_fqdn off
log_icp_queries off
cache_log none
cache_store_log none
## Dg ‘menipu’ dan memaksa sedikit supaya akses obyek lebih intensif di lokal Squid dan waktu simpan ditambah sebelum proses validasi terjadi (mis. validasi terjadi per 3 jam dg penyimpanan obyek terlama 3 bulan, utk ftp bisa lebih lama lagi)
refresh_pattern ^ftp: 10080 95% 241920 reload-into-ims override-lastmod
refresh_pattern . 180 95% 120960 reload-into-ims override-lastmod
## Toleransi aborting dihilangkan saja
quick_abort_min 0
quick_abort_max 0
quick_abort_pct 98
## Mematikan dan merekonfigurasi Squid jangan terlalu cepat krn bisa mengakibatkan integritas file kacau
shutdown_lifetime 10 seconds
## tidak perlu reservasi memori
memory_pools off
## Penting utk relasi dg sibling dg mengukur respons-nya via ICP dan ICMP (tapi ada isp yg tidak mengijinkan lho)
icp_hit_stale on
query_icmp on
## Penting utk meningkatkan refresh pattern lebih lanjut
reload_into_ims on
pipeline_prefetch on
vary_ignore_expire on
## Sekali lagi Squid diperlukan utk mengambil yg jaraknya jauh, jarak dekat langsung saja
acl local-dst dst semuaalamatlokal semuaalamatipygdekat
acl local-domain dstdomain localhost domain-anda.com isp-anda.com domainku.web.id
always_direct allow localhost local-dst local-domain
always_direct deny all
## Tidak begitu diperlukan
##ie_refresh on
================================================================================================================
saya mencoba proxy squid di fedora/redhat dengan konfigurasi sebagai berikut :
isi file squid.conf :
http_port 3128
icp_port 3130
tcp_outgoing_address 0.0.0.0
udp_incoming_address 0.0.0.0
udp_outgoing_address 0.0.0.0
cache_mem 16 MB
maximum_object_size 128 MB
cache_dir ufs /misc/squid/c1 7000 8 128
cache_dir ufs /misc/squid/c2 7000 8 128
cache_dir ufs /misc/squid/c3 7000 8 128
cache_access_log /var/log/squid/access.log
cache_log /dev/null
cache_store_log /dev/null
logfile_rotate 4
memory_pools_limit 8 MB
redirect_rewrites_host_header on
#replacement_policy GDSF
half_closed_clients on
request_header_max_size 128 KB
request_body_max_size 5 MB
dns_nameservers 192.168.0.200
quick_abort_min 16 KB
quick_abort_max 16 KB
quick_abort_pct 95
connect_timeout 120 seconds
peer_connect_timeout 30 seconds
#siteselect_timeout 4 seconds
read_timeout 15 minutes
request_timeout 5 minutes
client_lifetime 1 day
#———–transparent proxy ———–
httpd_accel_host virtual
httpd_accel_port 80
httpd_accel_with_proxy on
httpd_accel_uses_host_header on
#——————————————-
#Script Membuka/Menutup akses sex
acl sex url_regex -i “/etc/squid/sex”
acl blok-website url_regex -i “/etc/squid/blok-website”
acl QUERY urlpath_regex cgi-bin \?
no_cache deny QUERY
client_netmask 255.255.255.255
acl all src 0.0.0.0/0.0.0.0
acl localhost src 127.0.0.0/255.255.255.0
acl lan_ku src 192.168.0.0/255.255.255.0
acl images urlpath_regex -i \.gif$ \.png$ \.jpg$ \.jpeg$
acl Safe_ports port 80 21 443 563 70 210 8888 1025-9000 6661-7000
acl CONNECT method CONNECT
#http_access allow localhost CONNECT
#http_access allow internet CONNECT
#akses sex ditutup
#——————–
http_access deny sex
http_access deny blok-website
http_access allow CONNECT
http_access allow localhost
http_access allow all
http_access allow lan_ku
http_access allow Safe_ports
http_access deny !Safe_ports
http_access deny CONNECT
http_access deny all
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern . 0 20% 4320
#—————- administration info ————
cache_mgr [EMAIL PROTECTED]
cache_effective_user squid
cache_effective_group squid
#log_icp_queries off
#cachemgr_passwd mypassword all
#forwarded_for off
#buffered_logs on
visible_hostname gw.net
dan saya isi file rc.local :
#!/bin/sh
#
# This script will be executed *after* all the other init scripts.
# You can put your own initialization stuff in here if you don’t
# want to do the full Sys V style init stuff.
touch /var/lock/subsys/local
/etc/rc.d/init.d/routerrh
lalu isi file routerrh :
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A POSTROUTING -s 192.168.0.0/24 -d 0.0.0.0/0 -j MASQUERADE -o eth0
iptables -A FORWARD -s 192.168.0.0/0 -j ACCEPT
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -j MASQUERADE
iptables -t nat -A PREROUTING -i eth0 -s ! 192.168.0.200 -p tcp –dport 80 -j DNAT –to 192.168.0.200:3128
nah bagaimana menurut teman-teman ?
kok masih kurang kencang jalan internetnya, client saya memiliki 150 komputer ?
salam…..sys tunggu tanggapannya !!
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
http://sahir.dozer.or.id/wp/2005/07/11/setting-router-warnet/
|eth0
|
|——-|
| MGW |
|—|—|
|
|eth1
|
|
|——————–hub———————-|
| | |
| | |
| | |
|———| |———| |———|
|Client 01| |Client 02| |Client 03|
|———| |———| |———|
Pertama yang harus di lakukan adalah mensetting mgw(main gateway)
supaya bisa connect ke internet
Sebelum Mensetting :
1.Minta IP public ke ISP lengkap dengan netmask,broadcast dan dns nya
misalnya :
RANGE : 202.159.121.0/29
IP : 202.159.121.2
GATEWAY : 202.159.121.1
Nemast : 255.255.255.248
broadcast : 202.159.121.7
DNS1 : 202.159.0.10
DNS2 : 202.159.0.20
berarti kita mendapatkan ip 5 buah dari 202.159.121.2 – 202.159.121.6
2.Menentukan IP local yang akan kita gunakan buat client
Setting IP MGW :
1.[root@mgw cachak]$ vi /etc/sysconfig/network
lalu isi dengan :
NETWORKING=yes
HOSTNAME=mgw.domain.com
GATEWAY=202.159.121.1
lalu simpen dengan menekan :wq
2.Menconfigurasi IP eth0(default)
[root@mgw root]$ vi /etc/sysconfig/network-scripts/ifcfg-eth0
lalu isi dengan :
DEVICE=eth0
BOOTPROTO=static
IPADDR=202.159.121.2
BROADCAST=202.159.121.7
NETMASK=255.255.255.249
ONBOOT=yes
USERCTL=no
lalu simpen dengan menekan :wq
3.Setting dns resolve
[root@mgw root]$ vi /etc/resolv.conf
lalu isi dengan nameserver dari isp kita tadi :
nameserver 202.159.0.10
nameserver 202.159.0.20
lalu simpen dengan menekan :wq
4.Setting ip_forwarding
[root@mgw cachak]$ vi /etc/sysctl.conf
rubah net.ipv4.ip_forward = 0 menjadi net.ipv4.ip_forward = 1
atau kalau gak ada net.ipv4.ip_forward = 0 tambahin net.ipv4.ip_forward = 1
simpen dengan menekan :wq
5.restart network
[root@mgw cachak]$ /etc/init.d/network restart
Shutting down interface eth0: [ OK ]
Shutting down loopback interface: [ OK ]
Disabling IPv4 packet forwarding: [ OK ]
Setting network parameters: [ OK ]
Bringing up loopback interface: [ OK ]
Bringing up interface eth0: [ OK ]
[root@www root]#chkconfig –level 2345 network on
[root@www root]#
6.testing dengan ngeping ke default gateway 202.159.121.1
[root@mgw cachak]$ ping 202.159.121.1
PING 202.159.121.1 (202.159.121.1) 56(84) bytes of data.
64 bytes from 202.159.121.1: icmp_seq=1 ttl=63 time=0.356 ms
64 bytes from 202.159.121.1: icmp_seq=2 ttl=63 time=0.269 ms
64 bytes from 202.159.121.1: icmp_seq=3 ttl=63 time=0.267 ms
64 bytes from 202.159.121.1: icmp_seq=4 ttl=63 time=0.268 ms
— 202.159.121.1 ping statistics —
4 packets transmitted, 4 received, 0% packet loss, time 2997ms
rtt min/avg/max/mdev = 0.267/0.290/0.356/0.038 ms
7.testing untuk ngeping google.com untuk ngecek dns nya
kalau muncul :
PING google.com (216.239.39.99) 56(84) bytes of data.
berarti dns kita untuk mgw dah bekerja, tapi kalau muncul :
ping: unknown host google.com
berarti dns yang kita isikan di /etc/resolve.conf masih salah,
silahkan cek lagi ke ISP nya

nah bereskan sudah setting IP untuk mgw nya

supaya mgw ini bisa sekaligus di gunakan sebagai ns server
oleh client maka harus di install daemon bind atau
daemon nameserver yang lain
ataukalau sudah ada tinggal idupin Bind nya
[root@www root]# /etc/init.d/named restart
Stopping named: [ OK ]
Starting named: [ OK ]
[root@www root]#chkconfig –level 2345 named on
[root@www root]#
misalnya ip ke client adalah :
192.168.0.1/24
IP : 192.168.0.1
netmask : 255.255.255.0
broadcast : 192.168.0.255
RANGE IP CLIENT : 192.168.0.2-192.168.0.254
Setting ip untuk eth1 (yang ke client)
1.memberi IP 192.168.0.1 di eth1
[root@mgw cachak]$ vi /etc/sysconfig/network-scripts/ifcfg-eth1
lalu isi dengan :
DEVICE=eth1
BOOTPROTO=static
IPADDR=192.168.0.1
NETMASK=255.255.255.0
BROADCAST=192.168.0.255
ONBOOT=yes
USERCTL=no
lalu simpen dengan menekan :wq
2.Restart networknya
[root@mgw root]$ /etc/init.d/network restart
Shutting down interface eth0: [ OK ]
Shutting down interface eth1: [ OK ]
Shutting down loopback interface: [ OK ]
Disabling IPv4 packet forwarding: [ OK ]
Setting network parameters: [ OK ]
Bringing up loopback interface: [ OK ]
Bringing up interface eth0: [ OK ]
Bringing up interface eth1: [ OK ]
3.Testing dengan cara ping ip eth1
[root@mgw cachak]$ ping 192.168.0.1
PING 192.168.0.1 (192.168.0.1) 56(84) bytes of data.
64 bytes from 192.168.0.1: icmp_seq=1 ttl=63 time=0.356 ms
64 bytes from 192.168.0.1: icmp_seq=2 ttl=63 time=0.269 ms
64 bytes from 192.168.0.1: icmp_seq=3 ttl=63 time=0.267 ms
64 bytes from 192.168.0.1: icmp_seq=4 ttl=63 time=0.268 ms
— 192.168.0.1 ping statistics —
4 packets transmitted, 4 received, 0% packet loss, time 2997ms
rtt min/avg/max/mdev = 0.267/0.290/0.356/0.038 ms
Tinggal Setting IP computer client dengan ketentuan di bawah ini :
IP : 192.168.0.2 – 192.168.0.254
GATEWAY : 192.168.0.1
NETMASK : 255.255.255.0
BROADCAST : 192.168.0.255
NAMESERVER : 192.168.0.1
misal :
Client01
===============================
IP : 192.168.0.2
GATEWAY : 192.168.0.1
NETMASK : 255.255.255.0
BROADCAST : 192.168.0.255
NAMESERVER : 192.168.0.1
Client02
===============================
IP : 192.168.0.3
GATEWAY : 192.168.0.1
NETMASK : 255.255.255.0
BROADCAST : 192.168.0.255
NAMESERVER : 192.168.0.1
dan seterusnya sesuai banyaknya client,yang berubah hanya IP
untuk client windows maka setting IP
di bagian Start Menu/Setting/Control Panel/Network
setelah di setting ip client, maka coba ping ke 192.168.0.1
dari client,kalau berhasil berarti client dan MGW nya sudah tersambung.
Setting MGW supaya client bisa internat dengan menggunakan NAT
1.Matikan iptablesnya
[root@mgw root]# /etc/init.d/iptables stop
Flushing all chains: [ OK ]
Removing user defined chains: [ OK ]
Resetting built-in chains to the default ACCEPT policy: [ OK ]
[root@mgw root]#
2.Tambahkan iptables untuk Source NAt sesuai dengan ip di eth0
[root@mgw root]# /sbin/iptables -t nat -A POSTROUTING
-o eth0 -s 192.168.0.0/24 -j SNAT –to-source 202.159.121.2
[root@mgw root]# /sbin/iptables-save > /etc/sysconfig/iptables
[root@mgw root]# /etc/init.d/iptables restart
Flushing all current rules and user defined chains: [ OK ]
Clearing all current rules and user defined chains: [ OK ]
Applying iptables firewall rules: [ OK ]
[root@mgw root]# iptables-save
SNAT sudah,SNAT disini standar sekali dan gak ada proteksi
untuk mengetest nya kita browser di client lalau buka google.com,
kalau jalan berati kita sudah berhasil
+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
Hallo Linuxer …
Saya bikin proxy pake Squid versi 2.5.STABLE2. Udah bisa jalan dengan sukses. Thanks buat Mas Hanny Wijaya (hanny@rsds.or.id) *****)
Cuman ada masalah sama ISP, katanya broadcast saya kegedean sampe bikin flooding di jaringan dan bikin ping ke ISP nyampe 6000ms lebih. (O ya, koneksi saya ke ISP pake wireless)
Paket yang dikirim itu ICMP (Internet Control Message Protocol) yang kalau nggak salah itu adalah sejenis ping gitu..
Lha, ini konfigurasi saya :
#—————————————————————–
#NETWORK OPTIONS
#—————————————————————–
#NEIGHBOR SELECTION ALGORITHM
cache_peer rtp.us.ircache.net parent 3128 3130 login=xxx@xxx.com:xxxx
cache_peer sd.us.ircache.net sibling 3128 4827 login=xxx@xxx.com:xxxx
cache_peer pb.us.ircache.net sibling 3128 0 no-query default login=xxx@xxx.com:xxxx
icp_query_timeout 0
maximum_icp_query_timeout 2000
dead_peer_timeout 10 seconds
hierarchy_stoplist cgi-bin ?
acl QUERY urlpath_regex cgi-bin \?
no_cache deny QUERY
#—————————————————————–
#CACHE SIZE
cache_mem 256 MB
cache_swap_low 80
cache_swap_high 95
memory_replacement_policy lru
#—————————————————————–
#LOGFILE PATHNAMES AND CACHE DIRECTORIES
cache_dir diskd /usr/local/squid/var/logs 4000 16 256 Q1=64 Q2=72
#—————————————————————–
#EXTERNAL SUPPORT PROGRAMS
#Banner Blocker :
redirect_program /usr/local/squid/bannerfilter-1.21/redirector.pl
#—————————————————————–
#TUNING THE CACHE
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern . 0 20% 4320
#—————————————————————–
#TIMEOUTS
#—————————————————————–
#ACCESS CONTROLS
acl all src 0.0.0.0/0.0.0.0
acl manager proto cache_object
acl localhost src 127.0.0.1/255.255.255.255
acl to_localhost dst 127.0.0.0/8
acl SSL_ports port 443 563
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 563 # https, snews
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
# IIX network :
acl IIX dst_as 7597 7713 4795 4622 4787 4800
acl AA src 192.168.1.0/27
acl BB src 192.168.2.0/28
acl free_network url_regex -i 192.168.
acl 4user_only browser [-i] regexp opera OPERA Opera
acl 60user_only src 192.168.1.0/255.255.255.224
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow manager localhost
http_access allow localhost
http_access deny manager
http_access allow AA
http_access allow BB
http_access deny all
http_reply_access allow all
icp_access deny all
#—————————————————————–
#OWN RULES TO ALLOW ACCESS FROM CLIENTS
#—————————————————————–
#ADMINISTRATIVE PARAMETERS
cache_effective_user squid
cache_effective_group squid
visible_hostname xxxx–
#—————————————————————–
#CACHE REGISTRATION SERVICE
#—————————————————————–
#HTTPD ACCELERATOR
#—————————————————————–
#MICELLANEOUS
always_direct allow IIX
#—————————————————————–
#DELAY POOLS PARAMETERS
delay_pools 3
#pool no1 unlimited bandwith
delay_class 1 3
delay_access 1 allow free_network
delay_parameters 1 -1/-1 -1/-1 -1/-1
delay_access 1 deny all
#pool no2 limit bandwith 4kbits per second
delay_class 2 3
delay_access 2 allow 4user_only
delay_parameters 2 500/500 500/500 500/500
delay_access 2 deny all
#pool no3 limit bandwith 60kbits per second
delay_class 3 3
delay_access 3 allow 60user_only
delay_parameters 3 7500/7500 7500/7500 7500/7500
delay_access 3 deny all
#—————————————————————–
# TO ADD LATER :
#Porn Filter :
#acl porn url_regex “/usr/local/squid/etc/porn.txt”
#http_access deny porn
Kira-kira apa yang salah ya ..
Tolongin ya ..
THANKS A LOT !!
==============================================================================================================
lha, kok ujug2 pake eth1? btw, di pc nya ada brp NIC?
sshd nya listen ke ip apa aja?
coba pastein output dari ip addr sh
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
Btw, ini pake distro apa?
Ini saya kasih contoh skrip firewall sederhana (allow all in/out) yg cocok dipasang di mesin dgn distro turunan redhat.
(alasannya sih cuman karena ada bbrp program yg output/path nya beda di distro lain)
Cat: disini saya menggunakan iptables versi 1.3.8 dan kernel yg sudah memungkinkan utk meload modul” iptables secara otomatis
ada 3 file disini yg akan dipake. File tsb adalah interfaces, firewall, dan firewallku sbg file skrip iptablesnya sendiri
Di skrip ini, anda cuman ngedit file interfaces nya aja. Di file ini, anda cuman menentukan interface mana yg dipake utk ke internet dan interface mana yg akan dipake utk ke lan. Parameter” selebihnya akan diambil dari file firewall.
Pastikan anda mempunyai program sed, awk, ip (dari paket iproute2) dan ipcalc yg dari redhat atau turunannya.
(soalnya ada perbedaan antara output ipcalc yg versi redhat ama output ipcalc yg versi debian, shg harus ada modifikasi dikit kalo mau diterapin di mesin” debian)
Utk file interfaces, isinya sbb: (ntar file ini ditaruh di /etc/default/)
Code:
NETnic=ppp0
LANnic=eth1
Utk file firewall, isinya kurang lbh spt ini: (file ini jg ditaruh di /etc/default/)
Code:
# path ke executablenya iptables, diisi manual jg boleh
IPT=$(type -P iptables)
NETIP=$(ifconfig $NETnic |grep -w inet |cut -f2 -d”:” |cut -f1 -d” “)
LANIP=$(ifconfig $LANnic |grep -w inet |cut -f2 -d”:” |cut -f1 -d” “)
NETW=$(ipcalc -n $(ip addr sh $LANnic |grep -w inet |awk ‘{print $2}’) |cut -f2 -d”=”)
PREF=$(ipcalc -p $(ip addr sh $LANnic |grep -w inet |awk ‘{print $2}’) |cut -f2 -d”=”)
LAN=$NETW/$PREF
basic-tables(){
$IPT -F && $IPT -X && $IPT -t nat -F && $IPT -t nat -X && $IPT -t mangle -F && $IPT -t mangle -X
$IPT -I INPUT -i lo -s 0/0 -j ACCEPT && $IPT -I OUTPUT -o lo -d 0/0 -j ACCEPT
}
base_policy(){
local policy=$1
for base_policy in INPUT OUTPUT FORWARD; do $IPT -P $base_policy $policy; done
}
nat_policy(){
local policy=$1
for nat_policy in PREROUTING POSTROUTING OUTPUT; do $IPT -t nat -P $nat_policy $policy; done
}
mangle_policy(){
local policy=$1
for mangle_policy in PREROUTING OUTPUT; do $IPT -t mangle -P $mangle_policy $policy; done
}
isi file skrip iptables firewallku sbb: (jgn lupa diset executable, chmod u+x)
Code:
#!/bin/bash
. /etc/default/interfaces && . /etc/default/firewall
# bersihin dulu rule” sebelumnya, trus set default policy utk tabel filter, nat dan mangle
basic-tables && base_policy ACCEPT && nat_policy ACCEPT && mangle_policy ACCEPT
$IPT -t nat -A POSTROUTING -o $NETnic -s $LAN -j SNAT –to $NETIP
$IPT -A OUTPUT -o $NETnic -s $NETIP -d 0/0 -j ACCEPT
$IPT -A INPUT -i $NETnic -s 0/0 -d $NETIP -j ACCEPT
$IPT -A FORWARD -i $LANnic -o $NETnic -s $LAN -d 0/0 -j ACCEPT
$IPT -A FORWARD -i $NETnic -o $LANnic -s 0/0 -d $LAN -j ACCEPT
$IPT -A INPUT -i $LANnic -s $LAN -d $LANIP -j ACCEPT
$IPT -A OUTPUT -o $LANnic -s $LANIP -d $LAN -j ACCEPT
=================================================================================================================
saya pake fedora core 5, dengan kernel 2.6.16-1.2111_FC5
nah untuk script yang mas kasih bisa nih….trus saya juga punya script iptables lagi, klo script iptables yg ini bisa jalan, lancar, ini scriptnya :
Code:
#!/bin/bash
# Deklarasi variabel
LOKAL=”10.1.1.0/24″
BEBAS=”0.0.0.0/0″
# Interfaces
MASUK=”eth1″
KELUAR=”eth0″
# meload modul untuk iptables
/sbin/modprobe ip_tables
/sbin/modprobe ipt_MASQUERADE
/sbin/modprobe ip_conntrack
/sbin/modprobe ip_conntrack_ftp
/sbin/modprobe ip_conntrack_irc
/sbin/modprobe iptable_nat
/sbin/modprobe ip_nat_ftp
/sbin/modprobe ip_nat_irc
/sbin/modprobe iptable_filter
/sbin/modprobe ipt_REJECT
/sbin/modprobe ipt_REDIRECT
case “$1″ in
start)
echo “Menjalankan FIREWALL…”
/sbin/iptables -F
/sbin/iptables -F -t nat
/sbin/iptables -X
/sbin/iptables -X -t nat
echo 1 > /proc/sys/net/ipv4/ip_forward
echo 1 > /proc/sys/net/ipv4/tcp_syncookies
echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_broadcasts
echo 1 > /proc/sys/net/ipv4/ip_dynaddr
# Transparent proxy
/sbin/iptables -t nat -A PREROUTING -i $MASUK -p tcp -s $LOKAL –dport 80 -j REDIRECT –to-port 8080
# NAT
/sbin/iptables -t nat -A POSTROUTING -s 10.1.1.0/24 -o $KELUAR -j SNAT –to-source 192.168.1.109
# Larang paket dari luar jaringan untuk akses sharing
/sbin/iptables -A FORWARD -i $KELUAR -p tcp -s 0/0 –dport 137:139 -j REJECT –reject-with icmp-host-unreachable
/sbin/iptables -A FORWARD -i $KELUAR -p udp -s 0/0 –sport 137:139 -j REJECT –reject-with icmp-host-unreachable
/sbin/iptables -A FORWARD -i $KELUAR -p tcp -s 0/0 –dport 445 -j REJECT –reject-with icmp-host-unreachable
/sbin/iptables -A FORWARD -i $KELUAR -p udp -s 0/0 –sport 445 -j REJECT –reject-with icmp-host-unreachable
/sbin/iptables -A INPUT -i $KELUAR -s 10.1.1.0/24 -p all -j REJECT –reject-with icmp-host-unreachable
/sbin/iptables -A INPUT -i $KELUAR -s $BEBAS -p tcp –dport 22 -j REJECT –reject-with icmp-host-unreachable
/sbin/iptables -A FORWARD -i $MASUK -s $LOKAL -j ACCEPT
/sbin/iptables -A FORWARD -m state –state ESTABLISHED -j ACCEPT
# Ngeblock P2P
/sbin/iptables -A FORWARD -m ipp2p –kazaa –bit –gnu -j DROP
/sbin/iptables -A FORWARD -p tcp -m ipp2p –bit -j DROP
/sbin/iptables -A FORWARD -p udp -m ipp2p –bit -j DROP
/sbin/iptables -A FORWARD -p tcp -m ipp2p –gnu -j DROP
/sbin/iptables -A FORWARD -p udp -m ipp2p –gnu -j DROP
/sbin/iptables -A FORWARD -p tcp -m ipp2p –kazaa -j DROP
/sbin/iptables -A FORWARD -p udp -m ipp2p –kazaa -j DROP
sleep 2
echo
;;
stop)
echo “Mematikan FIREWALL…”
echo 0 > /proc/sys/net/ipv4/ip_forward
echo 0 > /proc/sys/net/ipv4/tcp_syncookies
echo 0 > /proc/sys/net/ipv4/icmp_echo_ignore_broadcasts
echo 0 > /proc/sys/net/ipv4/ip_dynaddr
/sbin/iptables -F
/sbin/iptables -F -t nat
/sbin/iptables -X
/sbin/iptables -X -t nat
echo “Firewall OFF… [OK]”
echo
;;
restart)
echo “Merestart FIREWALL…”
$0 stop
sleep 3
$0 start
echo
;;
esac
yang bikin bingung nih, kenapa script yang satunya ga jalan, walaupun policy setiap chain udah saya buat ACCEPT semua
===================================================================================================================
Ini output dari iptables-save dari skrip anda yg pertama yg saya edit sedikit Very Happy
Coba anda load pake iptables-restore.
Code:
## mangle table
*mangle

REROUTING ACCEPT [0:0]
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]

OSTROUTING ACCEPT [0:0]
-A PREROUTING -j ACCEPT
-A INPUT -j ACCEPT
-A FORWARD -j ACCEPT
-A OUTPUT -j ACCEPT
-A POSTROUTING -j ACCEPT
COMMIT
#
## filter table
*filter
:INPUT ACCEPT [0:0]
:FORWARD DROP [0:0]
:OUTPUT ACCEPT [0:0]
:LAN_INTERNET – [0:0]
-A INPUT -i lo -j ACCEPT
-A INPUT -i eth0 -p tcp -m tcp –dport 137:139 -j REJECT –reject-with icmp-host-unreachable
-A INPUT -i eth0 -p tcp -m tcp –dport 22 -j REJECT –reject-with icmp-host-unreachable
-A INPUT -i eth0 -p tcp -m tcp –dport 445 -j REJECT –reject-with icmp-host-unreachable
-A FORWARD -j LAN_INTERNET
-A FORWARD -p tcp -m tcp –tcp-flags FIN,SYN,RST,ACK SYN -m limit –limit 1/sec -j ACCEPT
-A FORWARD -p tcp -m tcp –tcp-flags FIN,SYN,RST,ACK RST -m limit –limit 1/sec -j ACCEPT
-A FORWARD -p icmp -m icmp –icmp-type 8 -m limit –limit 1/sec -j ACCEPT
-A OUTPUT -o lo -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p udp -m udp –dport 53 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -d 10.1.1.0/255.255.255.0 -i eth0 -o eth1 -p udp -m udp –sport 53 -m state –state RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p tcp -m tcp –dport 80 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -d 10.1.1.0/255.255.255.0 -i eth0 -o eth1 -p tcp -m tcp –sport 80 -m state –state RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p tcp -m tcp –dport 443 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -d 10.1.1.0/255.255.255.0 -i eth0 -o eth1 -p tcp -m tcp –sport 443 -m state –state RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p tcp -m tcp –dport 110 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p tcp -m tcp –dport 25 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -d 10.1.1.0/255.255.255.0 -i eth0 -o eth1 -p tcp -m tcp –sport 25 -m state –state RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p tcp -m tcp –dport 143 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -d 10.1.1.0/255.255.255.0 -i eth0 -o eth1 -p tcp -m tcp –sport 143 -m state –state RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -s 10.1.1.0/255.255.255.0 -i eth1 -o eth0 -p tcp -m tcp –dport 5050 -m state –state NEW,RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -d 10.1.1.0/255.255.255.0 -i eth0 -o eth1 -p tcp -m tcp –sport 5050 -m state –state RELATED,ESTABLISHED -j ACCEPT
-A LAN_INTERNET -j RETURN
COMMIT
#
## nat table
*nat

REROUTING ACCEPT [0:0]

OSTROUTING ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A POSTROUTING -s 10.1.1.0/255.255.255.0 -o eth0 -j SNAT –to-source 192.168.1.109
COMMIT
#
TAMBAHAN
#iptables -A POSTROUTING -s ip_lokal_anda/24 -o eth1 -p tcp -m tcp –dport 5050 -j SNAT –to-source ip_internet_anda
# id squid == > ada nggak ?
kalau tidak ada
# groupadd squid
# useradd -g squid squid
# vi /etc/squid.conf
cache_effective_user squid
cache_effetive_group squid <== sudah seperti inikah ?
ubah permission
# chown -R squid:squid /pathkesquid
partisi cache di ubah permisssionnya juga
# chown -R squid:squid /usr/local/cache
kalau partisinya terpisah di mount dulu
# /pathkesquid/squid -z ( buat direktori swap )
# /pathkesquid/squid
# netstat -nlp | grep squid <=== hasilnya apa ?
ngomong2 lebih flexibel kalau installasi squid-nya dari tarball saja
++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
# WELCOME TO SQUID 2.6.STABLE12
# —————————-
# NETWORK OPTIONS
# —————————————————————————–
http_port 8080
http_port 3128
hierarchy_stoplist cgi-bin ?
acl QUERY urlpath_regex cgi-bin \?
cache deny QUERY
acl apache rep_header Server ^Apache
broken_vary_encoding allow apache
maximum_object_size 256 KB
cache_replacement_policy lru
memory_replacement_policy lru
cache_dir diskd /cache/cache1 10000 46 256
cache_dir diskd /cache/cache2 10000 46 256
access_log /cache1/access.log squid
cache_log /cache1/cache.log
mime_table /etc/squid/mime.conf
pid_filename /var/run/squid.pid
cache_store_log none
log_mime_hdrs off
diskd_program /usr/libexec/diskd-daemon
##refresh Pattern ——-
############################################################################
refresh_pattern -i \.gif$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.jpg$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.jpeg$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.png$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.bmp$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.swf$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.co$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.GIF$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.JPG$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.JPEG$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.PNG$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.BMP$ 10080 88% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.avi$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.cab$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.mov$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.mp3$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.mpg$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.mpeg$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.aif$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.ra$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.rm$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.zip$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.rar$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.arj$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.tgz$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.exe$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.rpm$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.ace$ 20160 100% 40320 reload-into-ims override-expire override-lastmod
refresh_pattern -i \.tar\.gz$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.z$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.cue$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.tar\.gz$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.z$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.cue$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.msi$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.wsz$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.js$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.swf$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.txt$ 20160 100% 40320 override-lastmod
refresh_pattern -i \.exe$ 20160 100% 40320 override-lastmod
# —– Refresh Pattern untuk iklan
refresh_pattern -i .*banner.* 20160 100% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i .*ads.* 20160 100% 80640 reload-into-ims override-expire override-lastmod
refresh_pattern -i .*advert.* 20160 100% 43200 override-expire
refresh_pattern -i .*popups.* 20160 100% 43200 override-expire
refresh_pattern -i .*iklan.* 20160 100% 43200 override-expire
refresh_pattern -i .*art.* 20160 100% 43200 override-expire
refresh_pattern -i .*advertising\.com.* 20160 100% 43200 override-expire
refresh_pattern -i ^http://.*\.doubleclick\.net 10080 300% 40320 override-expire override-lastmod override-expire ignore-reload
refresh_pattern -i .*doubleclick\.net.* 20160 100% 43200 override-expire
refresh_pattern -i .*atwola\.com.* 20160 100% 43200 override-expire
refresh_pattern -i .*qksrv\.net.* 20160 100% 43200 override-expire
refresh_pattern -i .*burstnet\.com.* 20160 100% 43200 override-expire
refresh_pattern -i .*ad-images.* 20160 100% 43200 reload-into-ims override-expire override-lastmod
refresh_pattern -i .*yimg\.com/* 20160 100% 43200 override-expire
refresh_pattern -i .*img.* 20160 100% 43200 override-expire
refresh_pattern -i .*images.* 20160 100% 43200 override-expire
refresh_pattern -i .*photo.* 20160 100% 43200 override-expire
refresh_pattern -i .*advertising\.com.* 20160 100% 43200 override-expire
refresh_pattern -i .*static.* 20160 100% 43200 override-expire
refresh_pattern -i .*\.com\.com.* 20160 100% 43200 override-expire
refresh_pattern -i .*akamai\.net.* 10080 100% 20160 override-expire
# —— Refresh Pattern untuk News Sites ———–
refresh_pattern ^http://.*\.cnn\.com 360 50% 4320 override-lastmod override-expire ignore-reload
refresh_pattern ^http://news\.bbc\.co\.uk 360 50% 4320 override-lastmod override-expire ignore-reload
refresh_pattern ^http://.*\.ananova\.com 360 50% 4320 override-lastmod override-expire ignore-reload
refresh_pattern ^http://.*\.reuters\.com 360 50% 4320 override-lastmod override-expire ignore-reload
refresh_pattern ^http://.*\.astaga\.com 360 50% 4320 override-lastmod override-expire ignore-reload
refresh_pattern ^http://.*detik\.com.* 360 50% 4320 override-lastmod override-expire ignore-reload
# Inefficient sites
refresh_pattern microsoft 1080 150% 10080 override-expire override-lastmod override-expire
refresh_pattern msn\.com 4320 150% 10080 override-expire override-lastmod override-expire
refresh_pattern -i .*detik\.com.* 360 100% 10080 override-lastmod
efresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern .jpg 10000 30% 24000
refresh_pattern .png 10000 30% 24000
refresh_pattern . 0 20% 4320
quick_abort_min 16 KB
quick_abort_max 128 KB
quick_abort_pct 85
read_ahead_gap 16 KB
negative_ttl 5 minutes
positive_dns_ttl 6 hours
negative_dns_ttl 1 minute
range_offset_limit 4096 KB
acl all src 0.0.0.0/0.0.0.0
acl manager proto cache_object
acl localhost src 127.0.0.1/255.255.255.255
acl to_localhost dst 127.0.0.0/8
acl localmachine src xxx.xxx.xxx.0/24
acl localbackup src xxx.xxx.xxx.xxx/29
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
acl post method POST
http_access allow manager localmachine localhost localbackup
http_access deny manager
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
acl ip_client src xxx.xxx.xxx.0/24
http_access allow ip_client
acl ip_backup src xxx.xxx.xxx.xxx/29
http_access allow ip_backup
http_access allow localhost
http_access deny all
http_reply_access allow all
never_direct allow all
cache_effective_user squid
cache_effective_group squid
cache_mgr servas@servas-on.net
visible_hostname proxy.servas-on.net
forwarded_for on
log_icp_queries on
icp_hit_stale off
query_icmp off
coredump_dir /var/spool/squid
client_persistent_connections on
server_persistent_connections on
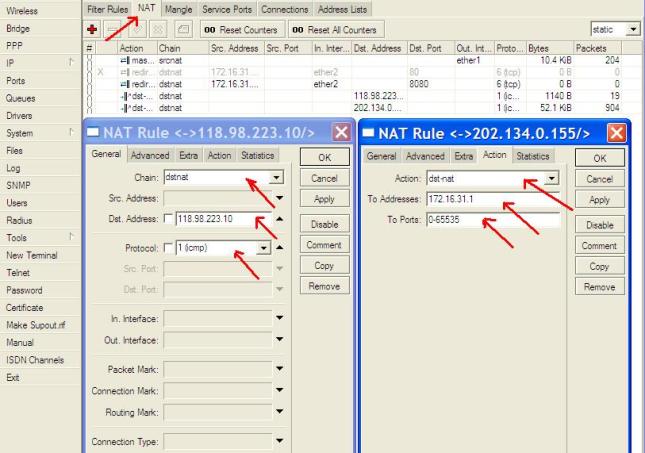

















![[Image: pic-squidbox.jpg]](http://paidjo.files.wordpress.com/2008/03/pic-squidbox.jpg)

